TECHNOLOGY
AI Ease Video Face Swap: Make Stunning Face Swap Videos Without Any Skills
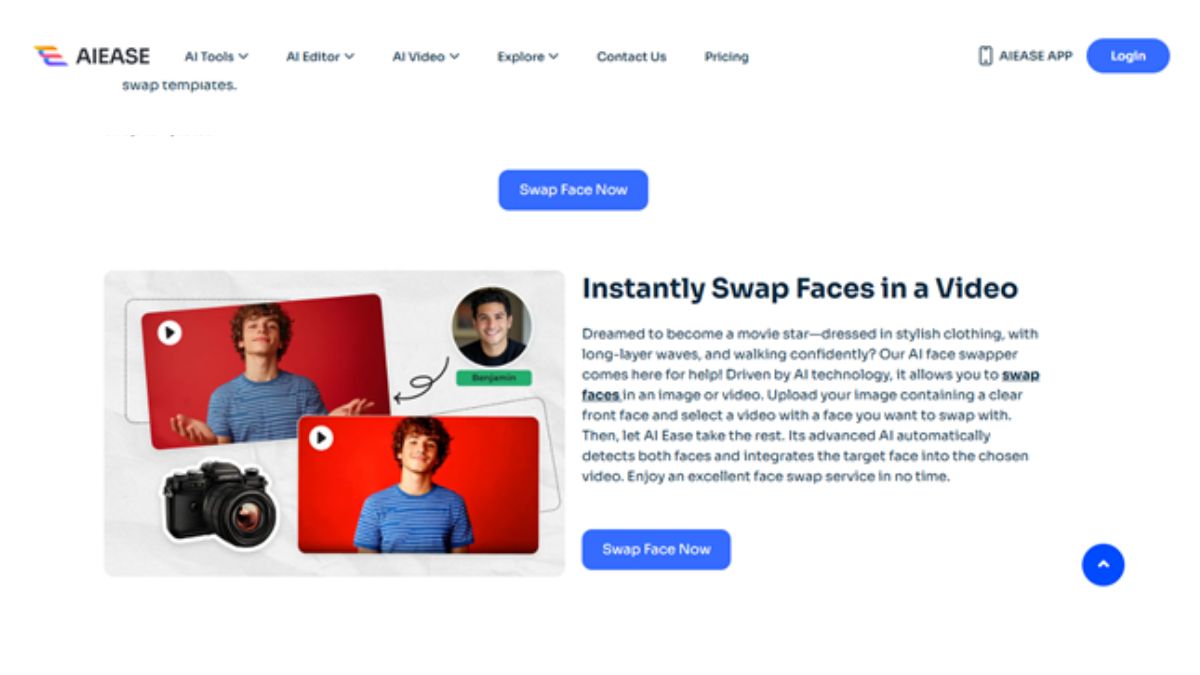
Do you ever want to make fun face swap videos, yet feel you can’t because you don’t know how to edit videos? You won’t need complex software or experience anymore, since now you can create great face swap videos with AI Ease.
The tool works automatically by using powerful AI technology. Creating funny, viral, or customized marketing videos is made easy and cost-free with AI Ease.
In the following section, we’ll talk about using AI Ease video face swap to create incredible face swap videos, what is so easy about it, and how you can try out the app yourself.
What Is AI Ease Video Face Swap?
AI Ease Video Face Swap is an easy-to-use online program that lets users swap faces in videos with the help of AI. You won’t need special skills or any additional software — everything can be done with your web browser. You only need to upload your images and videos, and the rest will be taken care of by AI Ease.
It takes advantage of AI technology to merge the faces and make the swap appear natural and smooth. AI face swap is compatible with people of any age, gender, or skin tone, so you always see good results.
With AI Ease, you can make videos for fun, develop your own social media content, or create marketing clips quickly and easily. It’s an excellent choice for people who are just starting to create face swap videos because you don’t need any difficult skills.
Why No Skills Are Needed to Create Stunning Videos
You don’t have to be an expert to use AI Ease, as it’s built for everyone to use easily. Because the interface is simple, you won’t encounter any challenging settings or tools. You don’t require any advanced skills to make exciting face swap videos with a few clicks.
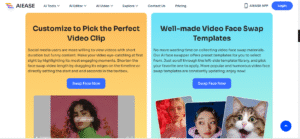
You don’t have to do everything yourself thanks to the pre-made video templates and automatic face detection. Just select a template or load your own video and face image, and AI Ease will finish the job without any problems. As a result, you do not have to worry about complex edits when being creative.
The processing is done quickly, meaning you can watch your face swap video almost right away. The application lets you create your own content and post it or use it in a flash.
AI Ease vs Traditional Methods: What Makes AI Ease Better?
1. Ease of Use
- No technical skills needed: AI Ease requires no video editing experience.
- Complex software required: Traditional methods often need advanced tools like Adobe After Effects.
- Simple drag-and-drop interface: AI Ease makes uploading and swapping faces easy.
- Manual timeline editing: Traditional editing involves complex timelines and frame adjustments.
2. Speed and Efficiency
- Fast processing: AI Ease completes face swaps in minutes.
- Time-consuming manual work: Traditional face swaps can take hours or days.
- Automated face detection: AI Ease seamlessly detects and blends faces.
- Frame-by-frame editing: Traditional methods require detailed manual work.
3. Accessibility
- Fully online: AI Ease works directly in your browser on any device.
- Software installation needed: Traditional tools require powerful hardware and setup.
- Mobile and desktop friendly: AI Ease works across multiple platforms.
- Desktop-only tools: Traditional editing is mostly limited to desktops.
4. Cost
- Free to start: AI Ease offers free credits for face swap videos.
- Expensive software: Traditional editing requires costly licenses or subscriptions.
- No need for professionals: AI Ease lets you create videos without hiring editors.
- Professional editing costs: Traditional methods often need expert help for the best results.
5. Quality and Realism
- AI-powered hyper-realism: AI Ease blends faces naturally with lighting and expressions.
- High skill required: Traditional methods can create quality swaps but need expertise.
- Seamless results: AI Ease produces natural-looking face swaps automatically.
- Less seamless without effort: Traditional swaps may look unnatural without extensive work.
Tips to Make Your Face Swap Videos Look Even Better
Face swap videos are simple to make with AI Ease, and a few tricks will help your videos look even better. If you try these methods, your videos will be better, more interesting to viewers, and give you amazing results. Try a few simple steps to make your face swap videos more impressive to your viewers.
Use High-Quality, Well-Lit Photos
- Choose clear, bright images for better face detection.
- Avoid blurry, dark, or pixelated photos.
- Ensure the face is front-facing and unobstructed
Choose Trending or Popular Video Templates
- Select videos that are currently viral on social media
- Use AI Ease’s updated library of popular templates.
- Pick clips that match your content style and audience
Keep Videos Short and Engaging
- Trim to highlight the most exciting moments
- Aim for 15–30 seconds for better viewer retention.
- Avoid long, dull sections that lose attention
Experiment with Different Faces and Clips
- Swap faces with friends, celebrities, or fictional characters
- Try mixing genres like comedy, drama, or music videos
- Test various combinations to find what works best
Preview and Adjust Before Finalizing
- Watch the generated video carefully for any glitches
- Adjust face images or clip length if needed
- Re-generate to improve smoothness and realism
Add Captions or Fun Effects
- Use captions to add humor or context
- Include stickers or emojis to increase appeal
- Add sound or music for more engaging videos
Your Next Viral Hit Is Just a Click Away—Try AI Ease Today!
Using advanced AI, it is now very easy to make great face swap videos. Because of its AI and ease of use, anyone can create hyper-realistic videos without having to be a professional or use expensive tools. You can quickly and easily produce entertainment for your friends, share viral posts, or make specific marketing videos using AI Ease. It is great for people who are new to makeup or experienced since it delivers instant, eye-catching results.
AI Ease is great because you can start right away since there’s no need to install anything. You can start swapping faces right away, using either your own videos and photos or the many fun templates available. Since the videos are high-quality and watermark-free, you can confidently share them anywhere. There has never been an easier time to share your videos on TikTok, Instagram, or YouTube.
So why wait? Try AI Ease Video Face Swap today and see how much better your video content can be. Enjoy this amazing tool with thousands of people who are already using it.
TECHNOLOGY
The Importance of Protocolo Operacional Padrao in Operational Efficiency

In today’s fast-paced business landscape, operational efficiency is more than just a buzzword—it’s a necessity. Companies are constantly searching for ways to streamline processes, reduce costs, and improve productivity. Enter the Protocolo Operacional Padrao (POP). This systematic approach serves as a roadmap for organizations aiming to achieve consistent results and enhance their overall performance. But what exactly does it entail, and how can it transform your operations? Let’s dive into the world of POP and discover its vital role in driving success across industries.
Understanding Protocolo Operacional Padrao (POP)
Protocolo Operacional Padrao (POP) refers to a set of standardized procedures designed to guide organizations in their day-to-day operations. It serves as an essential framework for consistency and quality across various tasks.
At its core, POP outlines specific steps that employees must follow when carrying out processes. This ensures that everyone is on the same page, regardless of individual experience or expertise.
Effective POPs include detailed instructions, checklists, and visual aids. These components help reduce errors and enhance overall workflow.
Companies across diverse sectors implement POPs to maintain regulatory compliance and improve service delivery. By establishing clear guidelines, they eliminate ambiguity and create a more structured work environment.
Understanding the principles behind Protocolo Operacional Padrao is crucial for any organization aiming for long-term growth and efficiency.
The Role of POP in Operational Efficiency
Protocolo Operacional Padrao (POP) serves as the backbone of operational efficiency. It establishes clear guidelines and procedures that employees can easily follow, minimizing confusion.
When a team understands their roles and responsibilities, workflow improves significantly. Time is saved as tasks are completed more efficiently without constant supervision or clarification.
Furthermore, POP aids in standardizing processes across departments. This consistency ensures that everyone is on the same page, which reduces errors and enhances productivity.
By implementing effective protocols, businesses can swiftly adapt to changes in demand or market conditions. Flexibility becomes an asset rather than a hurdle when teams know how to pivot seamlessly within established frameworks.
POP empowers organizations to streamline operations while maintaining high-quality standards. The result? Enhanced customer satisfaction and improved bottom-line results emerge naturally from this structured approach.
Benefits of Implementing Protocolo Operacional Padrao (POP) in Your Business
Implementing Protocolo Operacional Padrao (POP) brings numerous advantages to any business. First, it standardizes processes, ensuring consistent quality across all operations. This consistency builds trust with customers and stakeholders alike.
Another key benefit is improved efficiency. With clear guidelines in place, employees can execute tasks more swiftly and accurately, reducing downtime and errors. In turn, this leads to higher productivity levels.
Moreover, POP fosters a culture of accountability. When everyone understands their roles within the protocol framework, ownership increases. Employees are less likely to deviate from established practices when they know what’s expected.
Training new staff becomes easier as well. A comprehensive POP serves as a valuable resource for onboarding processes. It provides clarity on procedures that newcomers need to follow right away.
These benefits contribute significantly to an organization’s overall success and sustainability in today’s competitive landscape.
Tips for Developing a Successful Protocolo Operacional Padrao (POP)
When developing a Protocolo Operacional Padrao, start with clear objectives. Identify what processes need documentation and the goals you aim to achieve.
Involve your team early in the process. Their insights can provide practical perspectives that enhance effectiveness. Collaboration fosters ownership and commitment to the POP.
Structure the document logically. Use headings, bullet points, and tables for easy navigation. A well-organized POP is easier to follow and reduces confusion.
Test your protocols regularly. Gather feedback from users after implementation to spot areas needing improvement or updates. Iteration keeps your protocols relevant.
Training is crucial too. Ensure all employees understand how to use the POP effectively through workshops or training sessions tailored to different roles within your organization.
Maintain flexibility in your approach. As business needs evolve, so should your Protocolo Operacional Padrao. Regularly review it for necessary adjustments based on operational changes or industry standards.
Common Mistakes to Avoid with Protocolo Operacional Padrao (POP)
One common mistake businesses make with Protocolo Operacional Padrao is treating it as a one-time project. This approach leads to outdated procedures that can hinder efficiency over time. Regular updates are essential for keeping protocols relevant.
Another issue arises when organizations fail to involve employees in the development process. Ignoring frontline input can result in guidelines that are impractical or not user-friendly. Engaging staff fosters accountability and encourages adherence.
Additionally, some companies overlook training sessions after implementing POPs. Without proper education on new protocols, team members may struggle to adapt, leading to confusion and errors.
Neglecting documentation is a significant oversight. Comprehensive records ensure everyone understands their roles and responsibilities within the framework of POPs, promoting consistency across operations.
Case Studies: Successful Implementation of Protocolo Operacional Padrao (POP)
One notable case study involves a mid-sized manufacturing firm that adopted Protocolo Operacional Padrao (POP) to streamline its production line. By documenting each step of the process, they identified bottlenecks and implemented standardized procedures. This led to a 30% reduction in cycle time.
Another example is a healthcare facility that utilized POP for patient care protocols. The staff created clear guidelines for various medical procedures. As a result, they enhanced patient safety and improved compliance with regulations, reducing errors significantly.
An e-commerce company also embraced POP by standardizing its order fulfillment processes. This shift not only improved efficiency but also enhanced customer satisfaction through faster delivery times.
These real-world applications illustrate how tailoring Protocolo Operacional Padrao to specific industries can yield impressive results in operational effectiveness and overall business performance.
Conclusion: The Impact of Protocolo Operacional Padrao (POP) on Your Business’s Success
The implementation of Protocolo Operacional Padrao (POP) can significantly enhance your business’s operational efficiency. By standardizing processes, you create a consistent framework that drives productivity and reduces errors. This leads to improved quality in service delivery and customer satisfaction.
Companies embracing POP often see streamlined operations that free up resources for innovation and growth. Employees become more engaged when they have clear guidelines, which fosters a better work environment.
Furthermore, with the right protocols in place, businesses are equipped to adapt quickly to changes or challenges. This responsiveness is crucial in today’s fast-paced market dynamics.
Investing time and effort into developing an effective POP not only boosts efficiency but also positions your business as a leader within its industry. As you consider these elements, think about how implementing Protocolo Operacional Padrao could be the key step toward unlocking greater success for your organization.
TECHNOLOGY
Exploring Different Types of Video&a to Enhance Your Blog Posts

Introduction to Video&a Content
In today’s digital landscape, where attention spans are shorter than ever, capturing your audience’s interest can feel like an uphill battle. That’s where video&a content comes into play. Imagine being able to convey complex ideas through engaging visuals and dynamic storytelling—sounds appealing, right? Video has become a vital tool for bloggers looking to elevate their content and connect more deeply with their readers. Whether you’re sharing insights or personal stories, incorporating videos can make your posts not only more informative but also significantly more enjoyable.
As we dive deeper into the world of video&a content, you’ll discover how different types can resonate with your audience in unique ways. Get ready to explore various formats that will enhance your blog posts and keep viewers coming back for more!
Why Video is Important for Blog Posts
Video is a powerful tool that grabs attention instantly. It adds visual appeal to your blog posts, making them more engaging for readers. People are naturally drawn to motion and sound, which can help convey complex information quickly.
Additionally, video can boost your SEO efforts. Search engines favor rich media content, and having videos can increase the chances of appearing higher in search results. This means more traffic for your blog.
Moreover, videos foster connection with your audience. They allow you to showcase personality and authenticity in ways that text alone cannot achieve. When viewers see you or hear your voice, they feel more connected.
Integrating video enhances user experience on your site. Readers often prefer consuming information through visuals rather than long blocks of text. By offering varied formats like video you cater to different learning styles while keeping visitors engaged longer on your page.
Types of Video&a to Use in Blog Posts
When it comes to enriching your blog posts, various types of Video&a can make a significant impact.
Tutorial videos are particularly effective for demonstrating processes or explaining concepts in an engaging manner. Viewers appreciate the visual guidance that complements written instructions.
Product reviews and demonstrations add authenticity to your content. They allow readers to see products in action, which builds trust and encourages purchasing decisions.
Interviews and Q&A videos provide valuable insights from experts or influencers. These formats foster connection with your audience by answering their burning questions directly.
How-to video&a offer step-by-step instructions on specific topics, making complex information digestible.
Vlogs and behind-the-scenes footage create a personal touch. They invite viewers into your world, fostering a sense of community around your blog’s theme. Each type serves a unique purpose while enhancing reader engagement significantly.
Tutorial Videos
Tutorial videos are a fantastic way to provide value to your audience. They break down complex topics into manageable steps, making learning accessible and engaging.
By demonstrating a process visually, you help viewers grasp concepts more easily. This format can cater to different learning styles, which is always beneficial.
Whether it’s cooking recipes or coding tips, tutorial videos create an interactive experience. Viewers appreciate the chance to follow along in real-time.
Adding visuals and clear instructions enhances comprehension. This approach not only boosts viewer retention but also encourages sharing among peers.
With proper editing and pacing, these videos can maintain attention while delivering essential information. The right balance between detail and clarity keeps audiences coming back for more insights.
Incorporating tutorial videos into your blog posts will enrich the user experience significantly. It’s all about empowering your readers with knowledge they can apply immediately.
Product Reviews and Demonstrations
Product reviews and demonstrations are a fantastic way to engage your audience. They provide valuable insights into how a product performs in real life. This transparency builds trust with your readers.
Using video&a for these reviews allows viewers to see the product in action. It can highlight features, benefits, and even potential drawbacks that text alone might miss. A visual demonstration can effectively convey what makes the product stand out.
Consider including side-by-side comparisons with similar products. This approach not only informs but also empowers your audience to make informed decisions based on their needs.
Authenticity matters too—sharing personal experiences fosters connections. Encourage user-generated content by inviting customers to share their own videos alongside yours. This community aspect enhances engagement and enriches the overall conversation around the product.
Interviews and Q&A Videos
Interviews and Q&A videos offer a dynamic way to connect with your audience. They bring fresh perspectives and insights directly from industry experts or influencers. This format fosters engagement by allowing viewers to see real conversations unfold.
These videos can tackle trending topics, answer common questions, or dive deep into niche subjects. By including viewer-submitted inquiries, you make the content feel personalized and interactive.
Additionally, interviews create opportunities for storytelling. Guests share their experiences, challenges, and successes in an authentic manner. These narratives resonate with audiences looking for inspiration.
To make the most of this video type, focus on quality production values—clear audio and good lighting matter significantly. A relaxed setting helps participants feel at ease, leading to more genuine discussions that captivate viewers’ attention from start to finish.
How-To Video&a
How-To Video&a are powerful tools for engaging your audience. They provide step-by-step guidance, making complex topics more digestible.
These videos can cover a range of subjects. Whether it’s cooking, crafting, or technical skills, viewers appreciate clear instructions paired with visual demonstrations.
A well-crafted how-to video can boost the credibility of your blog by showcasing your expertise. Audiences tend to share helpful content, increasing visibility and driving traffic back to your site.
Keep your videos concise and focused. Aim for clarity in both visuals and narration. Using simple language helps ensure that everyone understands the material.
Incorporating captions can also enhance accessibility and engagement. It allows viewers to follow along easily without sound if needed.
Consider including common questions at the end of each video segment as well; this encourages interaction through comments and fosters a sense of community among followers.
Vlogs and Behind-the-Scenes Footage
Vlogs and behind-the-scenes footage offer an intimate glimpse into your creative process. They help to humanize your brand and build a deeper connection with your audience.
Viewers love seeing the real moments that happen off-camera. This type of content can showcase how ideas come to life, giving followers a sense of involvement in your journey.
Sharing personal anecdotes or challenges faced during production makes it relatable. It invites viewers to engage more deeply with what you create.
Behind-the-scenes videos can also highlight the tools and techniques used in your projects. This not only educates but inspires others who aspire to achieve similar results.
Moreover, these vlogs can be fun! Showcasing bloopers or candid moments adds authenticity while keeping things light-hearted for those tuning in. Engaging storytelling combined with raw footage creates compelling content that keeps audiences coming back for more.
Tips for Creating Engaging Video&a Content
Creating engaging Video&a content requires a blend of creativity and strategy. Start by knowing your audience. Understand their preferences and interests to tailor your videos accordingly.
Keep it concise. Aim for clarity while ensuring that you get straight to the point within the first few seconds. Attention spans are short, so capture interest quickly.
Use high-quality visuals and audio. Poor production can distract viewers from your message. Invest in a decent microphone and good lighting to enhance the overall quality of your videos.
Engage with storytelling. Share personal anecdotes or real-life examples relevant to your topic, making it relatable and memorable for viewers.
Encourage interaction by asking questions throughout the video or inviting comments at the end. This fosters a sense of community around your content, enhancing viewer connection.
Don’t forget to promote sharing across social media platforms; this expands reach organically!
Tools and Resources for Adding Video&a to Your Blog Posts
Adding Video&a to your blog posts can be streamlined with the right tools and resources. Start with video editing software like Adobe Premiere Pro or Final Cut Pro. These platforms offer robust features that allow for professional-grade edits.
If you’re looking for simplicity, explore online tools such as Canva or Animoto. They provide user-friendly interfaces and templates specifically designed for creating engaging videos quickly.
For hosting your videos, consider platforms like YouTube or Vimeo. Both offer customization options and easy embedding into your blog.
Don’t underestimate the power of stock footage websites either. Sites like Pexels or Unsplash feature high-quality clips that can enhance your content without breaking the bank.
Utilize social media integration tools to share your Video&a across different channels seamlessly. Tools like Buffer help in scheduling posts while ensuring maximum reach and engagement across various platforms.
Conclusion: Video&a
The integration of Video&a into your blog posts can significantly elevate the reader’s experience. With various types of video content available, you have ample opportunities to engage and inform your audience effectively. From tutorial videos that simplify complex topics to vlogs that provide a personal touch, each format serves a unique purpose.
Utilizing product reviews helps build trust with potential customers by showcasing real-life applications and experiences. Meanwhile, interviews and Q&A sessions add depth by featuring expert insights or addressing common queries from your readers.
Creating how-to videos allows you to demonstrate processes visually, making it easier for viewers to grasp information quickly. Behind-the-scenes footage humanizes your brand, offering a glimpse into the creation process and fostering a connection with your audience.
Remember, producing engaging Video&a content requires careful planning. Use tools designed for video editing and analytics to refine your work continuously. This ensures that every video added enriches the value of your blog posts while optimizing them for search engines.
Incorporating Video&a is not just about following trends; it’s about enhancing storytelling in an increasingly visual world. As you explore these avenues, you’ll discover new ways to captivate your audience while boosting engagement on your platform.
TECHNOLOGY
Speciering Explained: Why It’s Crucial for Targeted Content Creation

In today’s fast-paced digital world, capturing the attention of your audience is more challenging than ever. With a constant stream of content flooding every corner of the internet, standing out requires more than just creativity; it demands strategic precision. Enter speciering—a game-changing approach that tailors content to specific audience segments for maximum impact. This powerful technique goes beyond basic personalization and dives deep into understanding what truly resonates with different groups.
Imagine being able to create messages that speak directly to individual interests and needs, leading to higher engagement rates and stronger connections with your brand. Speciering helps you achieve this by refining your content strategy in ways that traditional methods simply can’t match. If you’re ready to elevate your marketing efforts and foster genuine relationships with your target audience, then understanding speciering is essential. Let’s explore how this innovative concept can transform your content creation process!
Understanding Speciering and Its Importance in Content Creation
Speciering is the art of segmenting your audience into distinct groups based on shared characteristics, preferences, or behaviors. It goes beyond traditional demographics by focusing on the nuances that drive individual choices and interests.
This approach recognizes that one-size-fits-all content often misses the mark. By understanding what motivates different segments, brands can create tailored messages that resonate more deeply with each group.
The importance of speciering in content creation cannot be overstated. When you deliver relevant information to specific audiences, engagement skyrockets. Customers feel understood and valued when they receive content crafted just for them.
Moreover, this targeted strategy enhances brand loyalty. People are more likely to connect with a brand that speaks directly to their needs and desires rather than generic messaging aimed at everyone. Embracing speciering opens doors to richer interactions and meaningful relationships between brands and their customers.
The Role of Personalization in Today’s Marketing Landscape
Personalization is transforming how brands interact with their audiences. It’s no longer enough to deliver generic messages and hope they resonate. Today, consumers expect tailored experiences that speak directly to their needs and preferences.
By leveraging data analytics, marketers can create profiles for different user segments. This allows businesses to craft content that feels relevant and engaging. Personalized emails, targeted ads, or even customized website interfaces can significantly enhance user experience.
Moreover, personalization fosters loyalty. When customers feel understood and valued, they are more likely to engage with a brand repeatedly.
This shift towards individualized marketing requires thoughtful strategies that align with consumer behavior trends. Brands must be agile in adjusting their approaches based on real-time feedback and insights gathered from customer interactions.
As competition increases, the ability to personalize becomes not just an advantage but a necessity in capturing attention in today’s crowded marketplace.
How Speciering Can Improve Target Audience Engagement
Speciering enhances audience engagement by allowing brands to tailor their content more effectively. When you understand the specific needs and preferences of your target segments, you can craft messages that resonate deeply.
By delivering relevant content, you’re not just selling a product; you’re addressing real problems your audience faces. This connection fosters trust and loyalty over time.
Additionally, speciering helps in segmenting communication channels. Different audiences prefer different platforms—some thrive on social media while others rely on email or blogs. Understanding these nuances enables brands to engage where it matters most.
When done right, this focused approach encourages interaction and feedback from users. It transforms passive readers into active participants in the conversation surrounding your brand, ultimately leading to higher conversion rates as well.
Techniques for Effective Speciering
To master speciering, start by segmenting your audience. Use demographics, interests, and behaviors to create distinct groups. This allows for tailored messaging that resonates deeply.
Next, leverage data analytics. Track user interactions and preferences across platforms. These insights reveal what content drives engagement.
A/B testing is another powerful technique. Experiment with different formats and messages within each segment. Analyze the results to refine your approach continually.
Incorporating feedback loops can enhance effectiveness as well. Encourage your audience to share their thoughts on your content through surveys or comments.
Stay agile in adapting strategies based on evolving trends and audience needs. Flexibility ensures you remain relevant in a fast-paced digital landscape.
Case Studies of Successful Brands Using Speciering
Nike is a prime example of effective speciering. The brand has mastered the art of personalizing content based on consumer behavior and preferences. By leveraging data, Nike creates tailored marketing campaigns that resonate with specific segments. This approach enhances user loyalty and drives sales.
Another standout is Spotify, which uses speciering to curate personalized playlists for users. Their algorithm analyzes listening habits to deliver unique music suggestions that keep listeners engaged. This level of customization increases user satisfaction and retention rates.
Coca-Cola’s “Share a Coke” campaign also highlights successful speciering. By printing individual names on bottles, Coca-Cola tapped into personalization at its core, creating emotional connections with consumers. This simple yet powerful strategy significantly boosted their sales and brand engagement.
These brands showcase how valuable targeted content can be when executed thoughtfully through speciering strategies.
Challenges and Limitations of Speciering
Speciering, while beneficial, isn’t without its hurdles. One major challenge is the data collection process. Gathering accurate information about your audience can be time-consuming and often requires significant resources.
Another limitation lies in the risk of over-segmentation. When audiences are divided into overly specific categories, it might isolate potential customers who don’t fit neatly into those boxes. This could lead to missed opportunities.
Additionally, maintaining relevance is crucial. Trends change rapidly, and what resonates with one segment today may fall flat tomorrow. Marketers must stay agile to adapt their strategies quickly.
There’s always the concern of privacy and compliance with data regulations like GDPR. Missteps here can damage brand trust and lead to legal ramifications that outweigh any benefits from speciering efforts.
Best Practices for Implementing Speciering in Your Content Strategy
To effectively implement speciering in your content strategy, start by building detailed audience personas. Understand their preferences, interests, and pain points. This foundational knowledge will guide your content creation.
Next, segment your audience based on these insights. Use demographic data and behavior patterns to create distinct groups that can be targeted with tailored messages. Remember, one size does not fit all.
Utilize analytics tools to monitor engagement across different segments. Track which types of content resonate most with each group. Adapt your approach based on real-time feedback for continuous improvement.
Incorporate dynamic elements into your content delivery. Personalization features like recommendations or customized emails enhance user experience significantly.
Ensure consistency in messaging across channels while maintaining the unique voice for each segment. Cohesiveness strengthens brand identity and fosters trust among diverse audience groups.
Conclusion
Speciering is more than just a buzzword in the marketing landscape; it’s an essential strategy for creating content that resonates. As consumers become increasingly discerning, personalized approaches are not just preferred; they’re expected. By understanding speciering and applying its principles, businesses can forge deeper connections with their target audience.
The role of personalization cannot be overstated. It helps brands stand out in a crowded marketplace where generic messages fall flat. Speciering allows companies to deliver tailored experiences that cater to individual needs and preferences, ultimately leading to higher engagement rates.
Effective techniques for speciering include audience segmentation, data analysis, and leveraging user-generated content. Brands that have embraced these strategies report significant improvements in user interaction and conversion rates. Real-world examples show how successful companies use speciering to drive results through targeted messaging.
However, challenges exist within this approach as well. Organizations must balance personalization with privacy concerns while ensuring they don’t over-segment their audiences into overly narrow categories that limit reach.
To effectively implement speciering within your content strategy requires adherence to best practices such as continuous testing and refining of content based on real-time feedback from audience interactions.
As you consider integrating these insights into your own marketing efforts, remember: the goal is not only about reaching your customers but also about truly connecting with them through meaningful conversations driven by relevant content.
-

 BUSINESS6 months ago
BUSINESS6 months agoBoost Your Brand with adsy.pw/hb3 Digital Solutions
-

 BUSINESS7 months ago
BUSINESS7 months agoTransform Your Business with MyWape
-

 TOPIC5 months ago
TOPIC5 months agoHow ATFBoru is Shaping Online Interaction in Unique Ways
-

 TOPIC6 months ago
TOPIC6 months agoHow Appfordown Simplifies Your App Experience: Tips and Tricks
-

 TOPIC8 months ago
TOPIC8 months agoWhy Wepbound is Revolutionizing the Way We Connect Online
-

 TOPIC6 months ago
TOPIC6 months agoSpeedyShort.com: Tips and Tricks for Effective Link Sharing
-

 TOPIC7 months ago
TOPIC7 months agoBehind the Screen: The Stories and Secrets of m0therearf
-

 TOPIC6 months ago
TOPIC6 months agoSimpcitt Decoded: Unlocking the Meaning Behind the Buzz
